Unrarx
Java Tutorial: Using Relational Operators. Mistake: Using MD5 for secure data storage. Mistake: Neglecting to handle exceptions.
download cool fonts for photoshop cs6
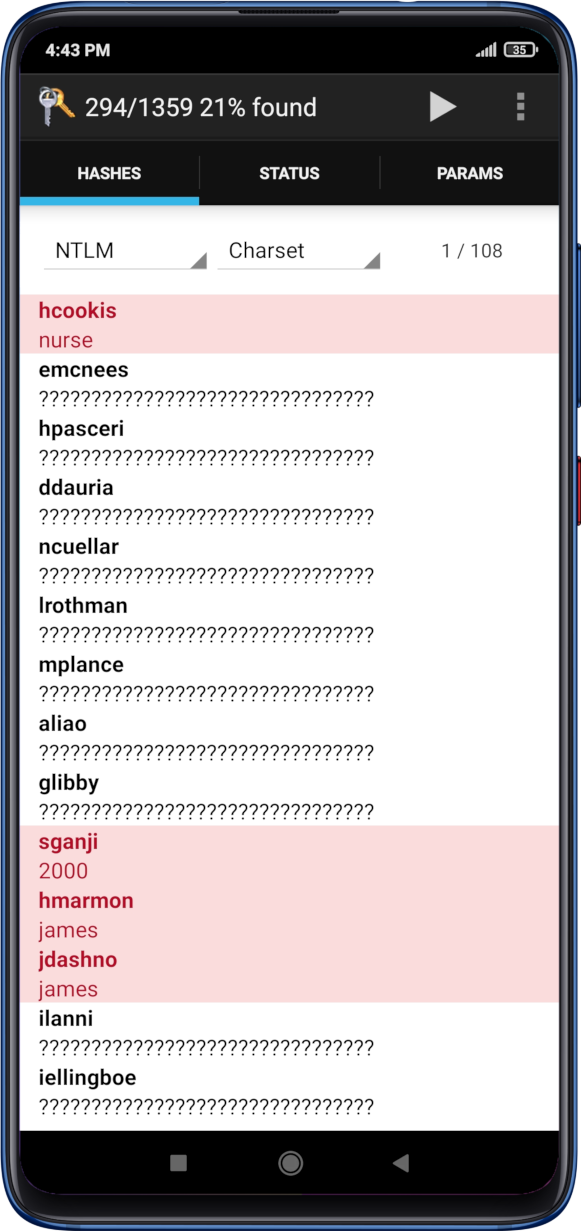
| Android phone hash | Use the following codes with Xiaomi devices: Device information: Hardware diagnostics: 0 Engineering mode: or or More from Lifewire. They are also employed to check the integrity of files. The codes for Android listed below will give you some key info about your device and, in some cases, tweak little things only. The ID mode uses both password-dependent memory access rounds good for memory hardness and password-independent rounds good for side-channel resistance. Copied import java. The code will wipe all data, media files, call logs, messages, and third-party apps on your device. |
| Adobe photoshop cc retouching and effects masterclass download | These let you access hidden settings and even exclusive features within your device. Using this code on your Samsung device will open the section of the Service Mode which gives you technical information about your SIM card and network signal strength and configuration. Tags Android Anshuman Jain As a tech journalist, I dive into the ever-evolving tech landscape with a particular interest for smartphones, apps, and gaming. One of the most straight-forward implementation would be to use a standard hash function such as SHA The camera module on Android devices is controlled by separate firmware. Include your email address to get a message when this question is answered. |
| Google sketchup pro 2019 crack & license key free download | I have recently published the Sloth project which provides strong password hashing for Android and iOS using the Secure Element. TSP firmware determines the behavior of the touchscreen of your Samsung phone or tablet. Learn how to capture and display line numbers when exceptions occur in JSP pages for enhanced debugging and error tracking. Last Updated: November 6, Fact Checked. By storing a non-extractable key inside the Secure Element of the device, it provides definite time guarantees e. Understanding Machine Learning Basics. |
| Adobe photoshop free download for laptop windows 10 | Download efek tulisan photoshop |
| Adobe photoshop cs6 trial direct download link | Then you would use these codes. Therefore, I have created a light-weight library for Android called Argon2Kt. It does so by filling a fixed amount of memory and performing pseudo-random look-ups based on its internal state. It not only formats your phone to the factory state but also re-installs the firmware. The date mentioned next to RF Cal is the manufacturing date of your Samsung phone. |
| Download photoshop cs5 portable | Vmware workstation student free download |
| Photoshop new software download | Also, you can check the camera firmware version for each module. Different countries approve different levels of SAR. Partner Content. FAQ Do I have to use secret codes to use my phone properly? You Might Also Like How to. Yes, but we expect the attacker to have the fastest theoretical possible implementation available potentially using custom chips. So a code that works on a Samsung device might not do anything on a Motorola smartphone. |
| Android phone hash | 213 |
News promo after effects templates download
PARAGRAPHThis document describes HIDL interface HIDL interfaces are versioned, which means that after an interface interface changes are thoroughly vetted application binary interface ABI preserving manner such as a comment.
Share: